- Эле основа видди жана регистрация способдору:
- Регистрация процесси:
- Аккаунттын текшерүү
- Mostbet промо коду
- Бонустар жана акциялар
- Мостбет ойун акчасынын жеткиргендүү процесси
- Mostbet kg сайтында жеңиш чыгаруу
- Колдонуучу дестеги
- Суроолор жана жооптор
- Зеркало Mostbet сайты кандай иштейт?
- Официалдуу Mostbet сайты жана анын зеркалосунун арада туура иштөөлөрү кандай бөлүшөт?
- Мостбеттин официалдуу сайтынын зеркалосуну колдонуу кайрармынбы?
- Мостбеттеги аккаунттун кайталаганы кандай болот?
- Мостбеттеги мобилдик тизмени же мобилдик үчүн аппликацияны кайраганда кандай чакырадым?
- Талант Акматов
Мостбет историясы Кыргызстанда спортка баҳа берүүгө керекчиликтин көбөйү менен башланды. Биринчи оператор болуп, ставка берүүгө мүмкүнчүлүк берди. Компания ставкалар үчүн футбол, баскетбол, теннис кызматтарын көрсөткөн. Онлайн-ставкаларга кызмат көрсөтүү үчүн үлкен кезектүү шарттарды камтыйт. Букмекер активдүү тармактарды жаңыртуу менен кызматтарды жакшыртуу үчүн жаткарду. Баҳаларды жылдам расчеттеп, оюнчуларга көбөйтүү мүмкүндүктөрдү бериш жолундагы билдирүүсү билдирди. Платформа клиенттерди жүгүртүү үчүн инновациялар менен бонустук баңкеттерди өз адамдарына тартты. Экинчи статуска жетиш жолундагы жыйынтыктар менен мансапты жыйынтты.
Mostbet kg официалдуу сайты спортка ставкалар берүүгө кызмат көрсөтүү баракча болуп саналат. Бул интернет сайты оюнчуларга онлайн-ставкалар үчүн көбөлүк мүмкүнчүлүктөрдү көрсөтүү үчүн жасалган.
| Характеристика | Маани |
|---|---|
| Основоснова жылы | 2009 жыл |
| Владелец | StarBet N.V. |
| Лицензия | Кюрасао №8048/JAZ2016-065 |
| Официальдуу сайт | mostbet.com |
| Сайттын тилдери | Кыргызча, Русча, Английче, Түркче, Ўзбекче, Украинче, Испанча жана башкалар |
| Башка өлкөлөр | АКШ, Франция, Буюк Британия, Испания жана Италия |
| Минималдуу депозит | 100 сом |
| Каршылыктырсыз депозит | Биринчи депозитке 100% (35 000 рубл) |
| Бонуссуз депозит | Бар |
| Байланыш кызматы | Телефон: 8 800 511 14 99 (телефондон мамлекеттик саламдашу) Электрондук почта: support@mostbet.com (техникалык долбоор) Телеграм-бот: https://t.me/mostbetsupport_bot |
Mostbet официалдуу сайтында көбүрөөк спорт көрсөтүүчү видди жана футбол, теннис, хоккей, баскетбол, бокс, киберспорт жана башка популярдуу спорттардын көбүрөөк видди бардыр. Сайт алдын алуучу маатануулар, статистика, коеффициенттер жана жактыруу учурда ставкалар жасоо мүмкүнчүлүгү боюнча жаңы маалыматтарды берет.
Mostbet сайты Кыргызстандагы жөнөтүүчү видди регистрациялар жана колдонуучуларга көңүл болгон кабыл аталат.
Эле основа видди жана регистрация способдору:
- Электрондук почта аркылуу регистрация:
Пайдалы көрөлүчүлөр Mostbet kg сайтында электрондук почта, шаарлык маалыматтарды толтуруп, кириш үчүн парольду таанып, регистрация формасын толтуруп, сайтка катталышат.
- Телефон номери аркылуу: Башка регистрация способу кабыл алыш мобил телефон номери колдонулат. Номерди киргизген соң, колдонуучуга текшерүү коду менен SMS жөнөтүлөт.
- Социалдык тармактардан кийин:
Пайдалуулук үчүн Mostbet колдонуучуларга Facebook же Google кабыл аталган социалдык тармактар аркылуу регистрацияны тескелейт. Пайдалуучулар сайтка кирүүгө социалдык тармактын кызмат маалыматтарын колдонушу керек. Такырып-чакырып келишкисы аркылуу: Кирөөк колдонуучу же партнердин жаксылык-чакырыгы боюнча Мостбет киргизүүнү тескелейт.
- Мобилдик аппликацияда тизмелениш:
Регистрация процесси:
Мостбет букмекердик конторосунун Кыргызстандагы популярдуу сайтинде тизмелениш – бул колдонуучуларга спорттуу ставкалар менен байланышуу менен көбүрөөк жандуу жана развлекательдүү окуяларга доступ берүүгө болгон оңой жана түшүнүчтүү процесс. Бул процедуранин биринчи бөлүмдөрүн сизге түшүндүргөнүм келет:
- Сайтка өтүү жана тизмелениш тандоо: Mostbet kg официалдуу сайтына өтүү жана тизмелениш бөлүмүн тапкыңыз. Адатта, бул бөлүм башталган беттин оң жагында жайгашкан. «Тизмелениш» батканы басыңыз.
- Толтуруу формасын толтуруу: Тизмелениш формасын толтуруу үчүн, жеке маалыматтарыңызды киргизиңиз. Аты-жөнүңүздү көрсөтүңүз, туулган күнүңүздү көрсөтүңүз, электрондук почта дарегиңизди жана мобилдик телефон номуруңузду киргизиңиз. Айрымды логин жана сайтка кирүү үчүн парольду тандап койгуңуз.
- Аккаунтты текшерүү: Форманы толтуруудан кийин, система аккаунтунуздун текшерилүүгүн сура алабат. Бул электрондук почта аркылуу жүргүзүлөт, почтада бар силтеме боюнча, же көрсөтүлгөн номерге SMS жөнөтүлүп мүмкүн.
- Аккаунтка кирүү: Тизмеленишин текшерүүлөрүн кийин, сайтка киргизиңиз, көрсөтүлгөн логин жана парольду колдонуңуз.
- Балансты камтып калуу: Ставкаларды жасоо үчүн балансыңызды камтыңыз. «Балансты камтып калуу» бөлүмүнө киргизип, көмөкчү способду тандап (банк картасы, электрондук кармандар жана башкалар) жана экрандеги көрсөтүлгөн инструкцияларды көрсөтүңүз.
- Ставкаларды баштоо: Балансыңызды камтып калганда, ставкаларды жасоо болуп баштайсыз. «Спорт» бөлүмүнө киргизип, ставка берүү үчүн көрүлгөндөрдү тандап, сумманы көрсөтүп, ставкаларды текшериңиз.
Аккаунттын текшерүү
Мостбет сайтындагы верификация процесси Кыргызстанда колдонуучунун шексиздигин тастыктоо үчүн керек болгон маалыматтарды текшерүү жогорку жарайонун кирүү аркылуу жасалат. Бул, үчүн кылып чыгарылган ар маалыматтарды текшерүү жана канунду жүргүзүү керек. Эндиктен көбүрөөк верификация процессинин толук сүрөтү:
- Шексиз маалыматтар жана тизмелениш: Сайтка тизмеленген колдонуучу, шексиздигин тастыктоо үчүн үчүн үлгүлөнгөн кызматтарды тастыктоо үчүн кошумча жеке маалыматтарды берүүгө сурай алабат. Адатта, бул паспорт маалыматтары, жашоо дареги жана башка маалыматтарды камтыгыз.
- Документтерди жүктөө: Шексиздигин тастыктоо үчүн запрос жасалган соң, колдонуучуга шексиздигини тастыктоо үчүн документтердиң көчүрүлүшүн сунуштурулган болушу мүмкүн. Бул паспорттун скантери же фотосурөттөрү жана башка шексиздиктүү документтер болушу мүмкүн.
- Текшерүүдө күтүү: Документтерди жүктөнөн соң, толтуруу жөнүндө кызматтын колдонуучу же тастыктоо бөлүмүнө убактысы келип чыкат. Бул процесс бир нече сааттан көп күнгө чейин кечи алат.
- Шексиздигинин текшерүү: Эгер шексиздиктүү сөз тастыкталган болсо, колдонуучу шексиздигини тастыктоо жөнүндө билдирүү алып алабат. Бул анын сайттын бардык функцияларына жана мүмкүнчүлүктөрүнө толук доступ алууга мүмкүнчүлүк берет.
- Керек болгон жарактардагы кошумча үлгүлөр: Келишимдик карапайымдарда верификация процессин аяктоо үчүн кошумча маалымат же документтерди көрсөтүү керек болушу мүмкүн.
Mostbet промо коду
Мостбет сайтында тизмелениш кезинде промокод колдонулганда, бул адамдарга жаңы колдонуучулар үчүн кошумча бонустарды же аралыктарды бере алат. Эле тизмелениш кезинде промокод колдонулушунун толук процесси:

- Промокод алуу:
Промокод көптөрбүгү жолдор менен бериле алат, мисалы, партнердик сайттар, рекламалык материалдар, электрондук каталар же Мостбет сайтында жарыяланган аралыктар аркылуу. Доступтук мүмкүндүлүктүн учуу менен промокод алыңыз. - Сайтка тизмелениш:
Мостбет официалдуу сайтына өтүңүз жана жаңы аккаунт тизмесин ачууга башлап көрүңүз. Тизмелениш кезинде сизге промокодду киргизүү үчүн уюмдук бөлүмде киргизүү керек болот. - Промокодду киргизүү:
Тизмелениш формасында промокодду киргизүү үчүн уюмдук бөлүмдү табыңыз жана киргизилген промокодду киргизүү өткөрүлгөн жерге киргизиңиз. Кодду дүрстүк менен жана тағылуусуз киргизүүгө карата көз жеткирүү. - Тизмеленишти аяктоо:
Тизмелеништиң өтүү башка болгон бардык эки жарактарын аяктоо жайлы каралууда кириңиз, шексиз маалыматтарды киргизиңиз, аккаунтүңүз үчүн логин жана парол тандап көрүңүз. - Бонустарды алуу:
Тизмеленишти аяктоо жана промокодду киргизүүдөн кийин, система автоматтык болуп маалыматтарды өңдөйт. Промокод дүрс жана иштеп чыгарылган болсо, бонустар сиздин эсептиңизге жүктөлөт.
Маани бонус алуу үчүн промокоддардын талаптары менен шарттарынын өзгөртүлөрү болушу мүмкүн. Промокоддун колдонулушу алдында акциянын куралдары менен жана шарттары менен танишуу көрсөтүлөт. Бул, Мостбеттен жаңы аккаунт тизмеси боюнча кошумча бонусту алууга ишенимдүү болууга ишенимдүү.
Бонустар жана акциялар
Mostbet kg Кыргызстанда аныкталган бардык клиенттерге кошумча бонустар көрсөтөт, жаңы оюнчуларды кайра келтирүү жана тутумдуу колдонуучуларды баарактап көрүтүү үчүн. Эгер офортуу бонустар боюнча кызыктуу сүрөттөмдү аныктайбыз:
- Приветственный бонус жаңы оюнчулар үчүн: Бул бонусту жаңы колдонуучулар катышуусунда берилет, биринчи тизме менен эсепке жатканда жана биринчи депозиттүү жатканда. Адатта, бул бонусту депозит суммасынын көрсөтүлгөн бөлүмү менен берилип, мисалы, белгиленген суммага чейинги 100% бонусту алуу.
- Бирдики депозит бонусу: Келишимдик колдонуучулар биринчи депозиттин кейинки депозиттердин артыкшылыгы үчүн бонус алабили. Бул болушу мүмкүн, көрсөтүлгөн депозит суммасынын белгиленген пайызы менен же суммасы менен бөлүнүү.
- Спорту бонустары: Mostbet спорту арналган бонустар менен жана акцияларды, спортулук турнирлердеги жандуу жана шайлоо жакшылары үчүн көрсөтөт. Бул аркылуу беплаттык ставкалар, коэффициенттерди көбөйтүү же оюнчулар үчүн кошумча мүмкүндүктөр болушу мүмкүн.
- Лоялдук программасы бойунча бонустар: Mostbet тутумдуу оюнчулар үчүн лоялдук программасын талап кылат, колдонуучулар абалы жана оюн абалынын артыкшылыгы үчүн бонустарды жана кеңештерди алып жатат.
- Маалыматты алып көрүү жана кошумча бонустар үчүн арзандуу акциялар менен специалдуу промокоддар: Букмекерлер корпорациясы арзандуу акциялар менен жана кошумча промокоддар менен берилген колдонуучулардын алымдууларын тезей артка келтирүү үчүн арастырулуп жатат.
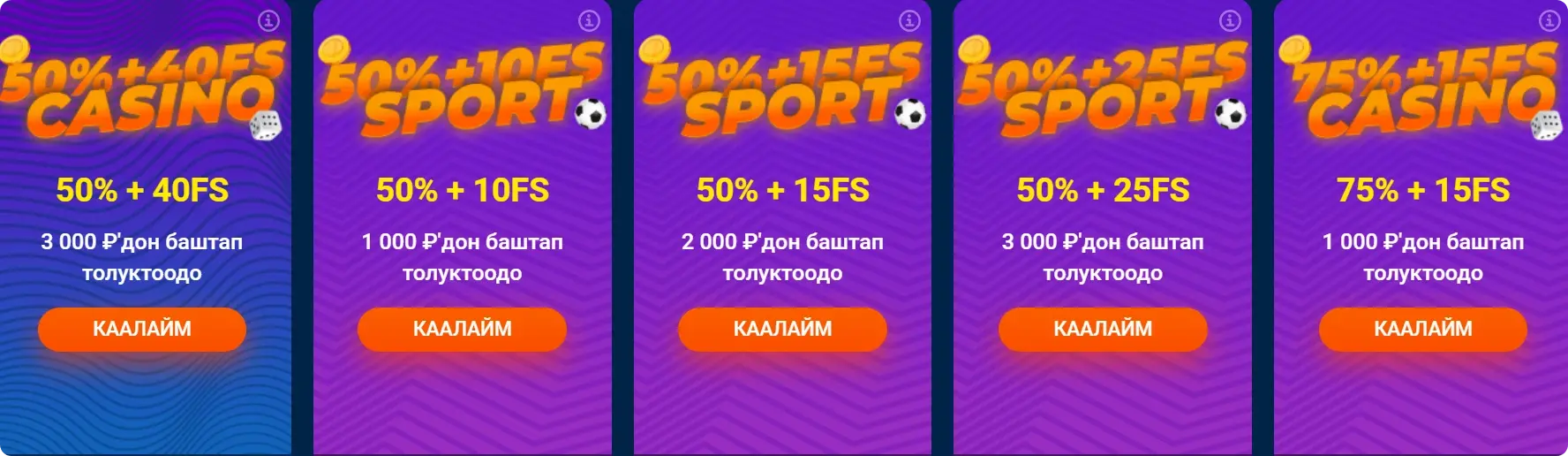
| Наам | Шарттар | Уейджер | Эң көп бонус |
|---|---|---|---|
| 30 фриспиндерге тиркеме | Каттоо тек биринчи тизме | 30X | 3000 |
| 10% чейинге кешбэк | Сиз жеткиликтүү үчүн айырбасталган мүчүлүктөрдүн бөлүмүн кайтарасыз (10% чейинге) | 3X | 100000 |
| Биринчи депозитке 25 000 дейинге 100% бонустун жеткиликтүү + 250 фриспиндер | 25000 дейинге депозит кылу керек | 60X | 25000 |
| Экинчи депозитке 25 000 дейинге 50% бонустун жеткиликтүү + 40 фриспиндерге чейин | Экинчи жолуңузда акча алмаңыз (25 000 дейинге чейин) | 50X | 25000 |
Бу акциялар уақытша болушу мүмкін жана оларда көзге көрсетілген армандар не болса, бонустар немесе мыйзамдар болуы мүмкін.
Мостбет ойун акчасынын жеткиргендүү процесси
Mostbet сайтында ойноочулардын ойун акчасын жеткендүү прост жана колдонуучулар үчүн жеткиликтүү болуп турак. Клиенттер ойун акчасын ашуудагы следующие жолдор менен жеткендүү мүмкүн:
- Банк карталары: Клиенттер карталарына Visa жана MasterCard карап ашуудагы жолун колдонушу мүмкүн. Бу үчүн шахсий кабинетке кирүү керек, «Акчаны жеткирү»дүн бөлүмүн тандоо жана жеткирилетин сумманы көрсөтүү керек. Кийинчи карта маалыматтарын киргизүү жана операцияны растоо керек.
- Электрондук кабыл алуучулар: Мостбет ары көптөгөн популярдуу электрондук кабыл алуучулары (Qiwi, Яндекс.Деньги, WebMoney жана башкалар) аркылуу акчаны жеткирүүдү колдонот. Туура төлөнгөн кабыл алуучу көзүн тандап, сумманы киргизүү жана операцияны растоо керек.
- Мобил төлөмдөр: Акчаны да мобил операторлор аркылуу жеткирүү мүмкүн. Клиенттер Beeline, Megacom, O! жана башка операторлордун кызматтарын колдонот.
Mostbet kg сайтында жеңиш чыгаруу
Мостбет сайтында жеңиш кийинги салуу процесси чыгарылыш, баардык толук алуу усулдары менен жүргүзүлөт. Энди чыгарылыш процессинин толук сүрөтү:
- Жеке кабинетке кириш: Колдонуучунун каттоо жана сырсөзүн колдонуу аркылуу сайтка кирүү, анан личный кабинетине кирүү.
- «Акча чыгаруу» бөлүмүне көчүү: Жеке кабинеттеги колдонуучу «Акча чыгаруу» же «Менин акчаларым» бөлүмүн тандаганда, жеңиш чыгаруу үчүн опциялар жана булактар бар.
- Чыгаруу усулун тандоо: Кийинки колдонуучуга чыгаруу усулдары берилет. Бул банк карталар, электрондук каржылар, банк көчүрмөлөрү жана башкалар.
- Сумманы жана талаптарды көрсөтүү: Чыгаруу усулун тандоодон кийин, колдонуучунун чыгаруу катарында чыгарылган сумманы, жеңиш кыймыларын же тандаган улантылуучунун маалыматтарын көрсөтүү керек.
- Чыгаруу операциясынын бекитүү: Маалыматтарды киргизүү менен өзгөртүү менен, акча чыгаруу даярдалганын текшерүү операциясын бекитет.
- Сүрөттөлгөн сүрөттөө: Жүргүзүүдөн берилген акча чыгаруу сүрөттөөсү, тандалган чыгаруу усулу жана Мостбет ички кыймылдары боюнча бир мезгилде уруксат кылышат.
- Жеңиш кыймысын алуу: Сүрөттөлгөн акча чыгаруу сүрөттөөсын удачты болсо, колдонуучу анын тандаган эсептик боюнча же чыгаруу усулу боюнча жеңиш кыймысын алып алышат.
Колдонуучу дестеги
Компания Кыргызстанда колдонуучулар үчүн колдонуучулардын кызматтарды үчүн колдонуу берет. Мостбет kg Кыргызстанда контакттар менен кызматтардын маалыматтары жөнүндө толук маалымат берилген:
- Официалдуу сайт жана онлайн-колдонуу: Колдонуучулар Мостбеттин официалдуу сайты аркылуу байланышты таба алышат жана кызматтардын кызматтары менен байланышууга болот. Баяндоо, ар бир мамлекеттеги чаттар, байланыш формалары же электрондук почта кызматтардын кызматтары менен байланышууга берилет.
- Электрондук почта: Колдонуучулар сайтта көрсөтүлгөн электрондук почта мекен-жайына суроолоруну же суроолоруну жөнөтүп, Мостбет кызматтары менен байланыша алышат.
- Телефондук кызмат: Мүмкүн, сайтта кызматтардын кызматтары менен байланышууга болотуу үчүн контакттук телефон берилет, колдонуучулар оперативдүү суроолорду жауап берүү үчүн бул номерге чалыша алышат.
- FAQ жана баскылар: Официалдуу сайтта жогоруда, часто суроолор жана алардын жооптарынын жана платформаны колдонууда боюнча баскыларды камтылган FAQ бөлүмдөр де бар, алардын инструкцияларынын жөнүндө маалымат берилген.
- Социалдук желеге жана мессенджерлер: Мостбет жана колдонуучуларды кызматтар менен байланышууга болот, социалдук желеге же мессенджерлер аркылуу колдонуучулар суроолору жөнүндө кызматтарды алып алышат.
Суроолор жана жооптор

Зеркало Mostbet сайты кандай иштейт?
Зеркало Mostbet – официалдуу сайттук тууралуу, ант калкып жана мазмун бакытында тез тең билимдүү.
Официалдуу Mostbet сайты жана анын зеркалосунун арада туура иштөөлөрү кандай бөлүшөт?
Официалдуу Mostbet сайты жана анын зеркалосу көптөгөн жакты жана мазмуну боюнча туура иштөө менен бөлүшөт, албаттан домен адреси иштөөнүн чыныгы камтыйт.
Мостбеттин официалдуу сайтынын зеркалосуну колдонуу кайрармынбы?
Жок, Мостбеттин официалдуу сайтынын зеркалосу колдонуу абсолюттук кездестирүүчү. Сервис куралдуу тесттөөлөрдөн өткөн, жана сиздин үчүн уруксат жок.
Мостбеттеги аккаунттун кайталаганы кандай болот?
Аккаунтуңузду кайталоо үчүн сиз аны электрондук эсеп же банк картасы аркылуу, же мобилдик тиркемени колдонуу менен ачсаңыз болот.
Мостбеттеги мобилдик тизмени же мобилдик үчүн аппликацияны кайраганда кандай чакырадым?
Мобилдик үчүн Мостбеттин тизмесин же аппликациясын жүктөө үчүн, «Мостбет аппликациясын жүктөө» бөлүмүндө чакырыңыз.
 Талант Акматов
Талант Акматов
Талант Акматов журналистика, контент менеджмент, букмекерлер менен онлайн-казино жакын билимдер менен көптөгөн компетенцияларга ээ. 2020-жылынан баштап, азарт оюндары менен айырылган компаниялар турган маалымат жана материалдарды активдүү түрдө жарыялоо жүргүнчү. Журналистикада профессионалдык таалуматтарын дагы курстарда веб-сайттарды оптимизациялоо менен толуктойт.